Table of Contents
Definition / general | Essential features | Terminology | Background | Applications | Implementation | Advantages | Limitations | Software | Diagrams / tables | Additional references | Board review style question #1 | Board review style answer #1 | Board review style question #2 | Board review style answer #2Cite this page: Wu K, Tsang P. Cybersecurity. PathologyOutlines.com website. https://www.pathologyoutlines.com/topic/informaticscybersecurity.html. Accessed March 31st, 2025.
Definition / general
- Cybersecurity in pathology and laboratory medicine refers to the protection of digital systems, networks and data from cyber threats and attacks, ensuring the confidentiality, integrity and availability of patient data
- Healthcare is an attractive target for cyberattacks for potential financial gain or malicious intent since patient records contain sensitive and private information and cyber defenses are generally vulnerable (Maturitas 2018;113:48)
Essential features
- Pathologists and clinical laboratory leaders should be proactive about network security, safeguarding patient information and preventing unauthorized access
- Cybersecurity strategies include implementing robust firewalls, intrusion detection / prevention systems and encryption protocols (J Appl Lab Med 2023;8:145)
- Remote access of patient information via mobile devices should involve data encryption, including for pathology reports and diagnostic images, to prevent unauthorized disclosure
- Regular system updates can ensure all software and systems used in pathology practice are up to date with the latest security patches to address known vulnerabilities
- Train pathologists and staff on cybersecurity best practices, including how to recognize phishing attempts and how to follow secure data handling protocols (Am J Clin Pathol 2022;157:814)
Terminology
- Information security: involves protecting patient data and digital records from unauthorized access, ensuring confidentiality, integrity and availability
- Data breach: unauthorized access or disclosure of patient information, which compromises patient confidentiality
- Phishing link: an internet link sent by cyberattackers that downloads malware when clicked or induces victims to disclose passwords or private information
- Ransomware: a malicious software that unlawfully restricts access to computer systems or locks data and demands a ransom payment to restore access, often spread by phishing links
- Malware: encompasses various harmful software designed to damage computer systems or steal electronic information
- Cyber threat intelligence: gathering and analyzing information about cybersecurity threats to proactively implement preventive measures and respond effectively to potential risks
Background
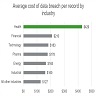
- Healthcare is a vulnerable industry with a high average cost per data breach due to the sensitive nature of patient records, which contain personal data and financial information (see Diagrams / tables)
- In 2019, the U.S. Food and Drug Administration (FDA) identified 11 areas of vulnerability whereby a cybercriminal could remotely control medical devices, such as changing or removing laboratory data (Digit Health 2021;7:20552076211059366)
- Hospitals and medical practices have generally lagged behind other industries in cyber defenses, making them an attractive target for cybercriminals
- WannaCry ransomware attack (AHA: Ransomware Attacks on Hospitals Have Changed [Accessed 30 August 2023])
- Global cyberattack on hospitals, medical practices and various diagnostic devices in 2017
- First ransomware to mass target medical devices, affecting 150 countries on the first day
- 1,200 devices affected and 19,000 medical appointments canceled
- Thought to be a politically motivated act of international terrorism
- Other recent incidents of cyberattack on health institutions are listed in the table below (J Med Ethics 2023;49:121, Am J Clin Pathol 2022;157:510, Int Cybersecur Law Rev 2022;3:147)
Institution Cyberattack incident Year Approximate downtime Comment 5 hospitals in the Waikato District Health Board (New Zealand) Ransomware 2021 Several weeks Attackers posted stolen data from 4,200 patients when ransom was not paid University of Vermont Medical Center Ryuk Ransomware 2020 Several weeks Malware infected 5,000 computers; disrupted elective procedures, laboratory data and medical appointments; financial loss estimated at > $63 million Dusseldorf University Hospital DoppelPaymer Ransomware 2020 Nearly 2 weeks Corrupted 30 servers and shut down emergency department, leading to fatality when patient had to be redirected to a more distant hospital LabCorp SamSam Ransomware 2018 1 week Affected multiple laboratories in the United States; impacted 7,000 systems and 1,900 servers; disrupted laboratory operations
Applications
- Defending against cyber threats
- Cybersecurity measures help pathologists and healthcare institutions defend against cyberattacks, e.g., ransomware, malware and data breaches, thus reducing potential disruption to patient care services and essential operations
- Protecting patient data
- Cyber defense strategies can safeguard patient health records and pathology data, preventing unauthorized access, theft or tampering with sensitive information
- Securing telepathology systems
- COVID pandemic has accelerated adoption of digital technologies and telepathology, creating a platform for potential security breaches
- Encrypted patient data and protected communication channels can allow pathologists to securely collaborate and share digital pathology images remotely
- Reference: Sensors (Basel) 2021;21:5119
Implementation
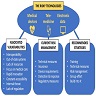
- See figure 2 in Diagrams / tables
- Security risk assessment
- Conduct a comprehensive assessment of the pathology practice's digital infrastructure to proactively identify vulnerabilities and potential risks
- Establish cybersecurity governance
- Develop and implement policies that outline security procedures, data handling guidelines and incident response protocols
- Employee training
- Adequate training for pathologists and laboratory staff, emphasizing the importance of cybersecurity best practices
- Password management, recognizing phishing attempts, responsible use of social media and personal mobile devices and reporting security incidents (Am J Clin Pathol 2022;157:814)
- Adequate training for pathologists and laboratory staff, emphasizing the importance of cybersecurity best practices
- Network and system protection
- Regular system updates and patching to ensure all software and systems used in pathology practice contain the latest security patches to address known vulnerabilities
- A zero trust security control strategy involves performing preimplementation due diligence on all new software and network connected medical devices (J Appl Lab Med 2023;8:145)
- Deploy firewalls, intrusion detection / prevention systems and antivirus software to safeguard networks and devices
- Firewall is the first line of digital defense for protecting healthcare network from the public internet, aimed at blocking malware from being installed and preventing unauthorized access of protected health information
- Implement access controls of pathology information: employing role based remote access privileges (specific to pathologists, administrative staff and technical staff) and multifactor authentication can limit potential breaches
- Incident response plan
- Develop a clear incident response plan to rapidly address and contain cybersecurity breaches
Advantages
- Data protection
- Cybersecurity measures safeguard patient data, preserving patient privacy and confidentiality of personal information
- Laboratories and hospitals have a social responsibility to proactively deter and block cyberattacks by hackers
- Continuity of services
- By preventing cyberattacks and data breaches, healthcare organizations can ensure uninterrupted access to their information systems and medical devices essential for providing patient care
- Cyberattack related downtime in pathology and laboratory information systems is associated with operational inefficiency, service disruption and an elevated risk of medical errors related to manual processes
- Regulatory and standard compliance
- Adhering to cybersecurity standards helps the pathology practice comply with data protection laws and healthcare regulations, such as the Healthcare Insurance Accountability and Portability Act of 1996 (HIPAA)
- References: J Appl Lab Med 2023;8:145, J Clin Monit Comput 2023 Apr 24 [Epub ahead of print]
Limitations
- Practical issues related to cost, resources and expertise
- Implementing comprehensive cybersecurity measures may involve significant initial costs and ongoing maintenance expenses; however, cyber breaches due to inadequate security can cause even more financial damage as well as loss of patient trust (Technol Health Care 2017;25:1)
- Inadequate access to cybersecurity experts knowledgeable in healthcare may be a source of vulnerability
- Human errors
- Despite security measures, human errors, such as insecure data handling and falling victim to phishing attacks, can still be a source of security risk
- Paying ransom does not guarantee easier recovery
- 80% of small to medium companies that paid the ransom historically did not receive the decryption key as promised (Digit Health 2021;7:20552076211059366)
- Evolving threats
- As cyber threats continue to evolve, staying ahead of attacks requires continuous updates and improvements to cybersecurity protocols (Technol Health Care 2017;25:1)
Software
- Symantec Endpoint Security
- Comprehensive cybersecurity solution that offers antivirus, firewall and intrusion prevention capabilities to protect against various threats
- McAfee Total Protection
- Provides antivirus, antimalware and encryption features to safeguard data and devices from cyber threat
- Cisco Umbrella
- Cloud delivered security service that offers protection against threats, such as malware, ransomware and phishing attacks
Diagrams / tables
Additional references
Board review style question #1
Which of the following shows the correct definition of a term related to cybersecurity or cyberattack?
- Data encryption: harmful software designed to steal sensitive electronic information
- Firewall: a security measure that automatically triggers a police report when a cyber threat is detected
- Phishing: the practice of sending email messages to alert patients that laboratory results are available in the patient portal
- Ransomware: malicious software that locks or encrypts data, restricts access to computer systems or devices and demands a ransom payment to restore access
Board review style answer #1
D. Ransomware is malicious software that locks or encrypts data, restricts access to computer systems or devices and demands a ransom payment to restore access. It is a type of cybercrime aimed at extorting money. Answer C is incorrect because phishing involves sending an email or internet link that downloads malware when clicked on or induces victims to disclose passwords and private information. Answer B is incorrect because firewalls are a security measure that protects computer networks by blocking malware from being installed. Answer A is incorrect because data encryption involves encoding sensitive information that can only be accessed or decoded by a user with the correct encryption key.
Comment Here
Reference: Cybersecurity
Comment Here
Reference: Cybersecurity
Board review style question #2
Which of the following practice patterns can increase the risk of a cyberattack?
- Adopt a zero trust security control strategy that mandates due diligence conducted on all new software
- Increase staff's awareness of potential phishing attempts on their work email
- Delay implementation of software updates of the laboratory information system
- Deploy firewalls, intrusion detection / prevention systems and antivirus software
Board review style answer #2
C. Delay implementation of software updates of the laboratory information system. Delaying software updates poses a risk because regular system updates and patching are necessary to ensure that information systems contain the latest security patches. Answer D is incorrect because deploying firewalls, intrusion detection / prevention systems and antivirus software is an effective cyber defense strategy. Answers A and B are incorrect because increasing awareness of potential phishing attempts and adopting a zero trust security control strategy on new software can reduce the risk of a cyberattack.
Comment Here
Reference: Cybersecurity
Comment Here
Reference: Cybersecurity